Are Crypto Wallets Safe? — Tips to Ensure Maximum Protection of Your Digital Assets.
Sep 18, 2023

Cryptocurrency and blockchain have been at the forefront of technology for many years, and as the industry continues to grow, investors are drawn to its potential. However, with this rise in popularity comes an increase in security concerns. According to cybersecurity firm Certik, nearly $1 billion in cryptocurrency has been pilfered due to scams, rug pulls, and exploits through the first half of 2023 alone.
Thus, for investors looking to dip their toes into the crypto world, understanding and taking measures to protect their cryptocurrency is essential. As crypto wallets are the main storage point of digital assets, it pays to understand what they are and how to protect them.
Key Takeaways:
- Cryptocurrency wallets are digital storage points for cryptocurrency where private and public keys are kept.
- Hot wallets are best for quick transactions and everyday usage, while cold wallets provide enhanced security and peace of mind for storing large amounts of cryptocurrency over an extended period of time.
- Cryptocurrency wallets are vulnerable to common security risks such as scams, phishing, malware attacks, and the loss of private keys or seed phrases, so users must take extra precautions to protect their funds.
- Crypto wallet security tips include using strong passwords and two-factor authentication, employing secure internet connections, storing private keys offline, regularly backing up wallets, and being aware of scam schemes.
What Are Crypto Wallets?
A cryptocurrency wallet is a device or program that is used to send and receive cryptocurrencies and digital assets securely. It acts as a digital counterpart to a physical wallet used to store physical currency. However, it’s important to note that while a physical wallet holds money, a crypto wallet doesn’t store crypto assets within it.
To draw a parallel, let’s consider something most people already have in their physical wallets: a debit card. Just like a crypto wallet, a debit card is not money itself, but it grants access to your money. However, there is a key difference. While a debit card is controlled by a centralised entity like a bank, crypto operates in a decentralised manner, meaning no person or organisation controls it. This distinction necessitates that crypto wallets function differently from traditional bank accounts.
Public And Private Keys
Two crucial pieces of information in a crypto wallet are the public crypto address and the private key:
- The public address is akin to the account number on a debit card, enabling others to send cryptocurrencies to that address.
- On the other hand, the private key is comparable to a password for the debit card, as it grants access to the crypto associated with the corresponding public address. Notably, a private key is a 256-bit secret number.

Managing the private key is one of the primary functions of a crypto wallet. It is a crucial aspect that ensures the security and control of one’s digital assets.
Whenever an investor transfers crypto from one wallet to another, they use their private key to access the funds and send them to the new wallet owner. As such, these keys should be kept secret, as someone obtaining the private key would have access to all of the funds in the wallet.
Recovery Phrase
But how to secure your private keys? To provide a user-friendly approach, crypto wallets use a recovery phrase, secret passphrase, or seed phrase. This recovery phrase adds an extra layer of protection by generating a list of words, usually between 12 and 24, which can be used to reconstruct the crypto wallet. Even if the original wallet is lost or destroyed, the recovery phase allows users to regain access to their funds, ensuring peace of mind and safeguarding their valuable assets.
What Types of Wallets Are There?
Crypto wallets come in two varieties: hot and cold.
Hot Storage
A hot wallet is one that is connected to the internet, and as such, it’s vulnerable to outside attacks.
Hot wallets are available online through cryptocurrency exchanges or specialised platforms that provide storage services for digital currencies. Users rely on these services to safeguard their private keys, which are stored and encrypted within the online application itself.
However, it’s important to acknowledge that using a hot wallet can involve certain risks due to the increased accessibility of funds held within. These wallets are more vulnerable to potential exploits by hackers or malware programs, which could compromise the security of the stored funds. Therefore, users must exercise caution and implement additional security measures when utilising hot wallets in order to mitigate these inherent risks.
Hot wallets are typically useful for quick transactions and everyday usage. However, due to their online nature and potential vulnerability to hacking, they may not be the most secure option for storing substantial amounts of cryptocurrency over an extended period of time. It is important to consider alternative storage solutions, such as cold wallets or hardware wallets, for enhanced security and peace of mind.
Cold Storage
A cold wallet is a device that enables users to store their private keys offline. As the funds are not accessible online, there is no risk of them being hacked or compromised by malicious actors.
Cold wallets come in both physical and digital forms, with the most popular type of cold storage being hardware wallets. These devices provide extra layers of security through the use of external security chips and often come with a recovery phrase for an extra security layer.
Unlike hot wallets, cold wallets can be used to store cryptocurrencies over an extended period of time without the risk of funds being compromised or stolen. As such, it is recommended that users keep large amounts of crypto within cold storage rather than hot wallets.
Given that hot wallets allow for quick transactions versus cold wallets, ensuring better safety and security of digital assets, many investors opt for both in order to balance convenience with optimal protection.
What Are the Main Security Risks When Using Crypto Wallets?
One of the primary objectives of holding your crypto is to ensure the utmost security of your private keys and seed phrases. If these are compromised, the funds stored in the crypto wallet may be irrevocably lost. Hence, it is essential to understand and mitigate the security risks associated with storing digital assets.
The most common security threats include:
Scams
Cryptocurrency has gained immense popularity as a form of currency. However, it has also become a prime target for scammers. The anonymity and lack of regulation associated with crypto can make it challenging to identify fraudulent schemes. Stay vigilant and be aware of common tactics like Telegram scams, giveaway scams, and other schemes employed by criminals to deceive investors and take their hard-earned money.
Maintaining funds on a centralised exchange
Centralised exchanges are online platforms that facilitate the trading of digital assets. As they are connected to the internet, these exchanges can be vulnerable to hacking and other malicious threats. Thus, it is generally recommended to avoid keeping your funds on these services for any extended period of time.
Phishing
Phishing is a type of cybercrime where attackers aim to steal an individual’s confidential information, like private keys or passwords. They often employ deceptive emails and malicious links to trick users into revealing sensitive data.
Malware attacks
Malware attacks involve downloading malicious software onto devices, which can compromise the security of personal data and digital assets. Malware typically comes in the form of spyware or ransomware that threatens to take control over user devices until they pay a certain amount. To protect your crypto, it is important to keep your devices secure by regularly updating software with anti-malware programs.
Losing your private keys or seed phrase
Losing your private keys or seed phrases can have dire consequences when it comes to managing your crypto assets. Safeguard your vital information, for it holds the key to maintaining full control and ownership over your valuable assets.
Crypto Wallet Security Tips
So, what can you do to protect your crypto wallet? Here are some tips that will help you keep your funds secure:
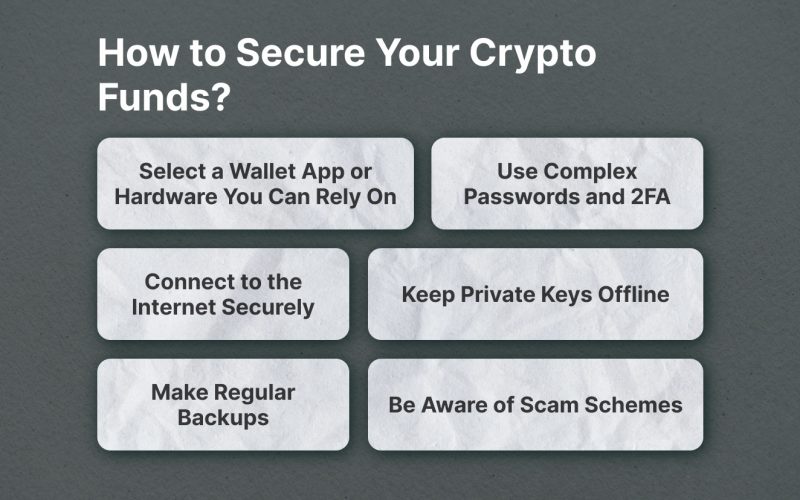
Select a Wallet You Can Rely On
It is important to choose a wallet that comes from a reputable provider, as this can help reduce the risk of potential exploits by hackers and malicious actors. For example, exchange wallets are typically less secure than dedicated crypto wallets, as the custodian has full control over user funds, leaving users vulnerable to potential scams and hacks.
At the same time, if you want to hold a large amount of crypto, you should consider using a hardware wallet, as it offers improved security and additional layers of protection.
When it comes to wallets, it’s important to pay attention to reviews. Consistently bad reviews should raise a red flag. However, the weight of the reviews matters. If they mainly focus on the user interface, it may not pose a significant security risk. But if the reviews mention a lack of security measures, this could be a sign that you should look elsewhere.
Use Complex Passwords and 2FA
One way to ensure the security of your funds is by using a strong password that includes a combination of uppercase and lowercase letters, numbers, and symbols. This will make it significantly more difficult for unauthorised individuals to gain access to your wallet.
In addition to a strong password, it is highly recommended to enable two-factor authentication (2FA) whenever possible. This additional layer of protection adds an extra step to the login process, requiring a secondary verification method, such as a code generated on your mobile device, to access your wallet. By implementing 2FA, you greatly reduce the risk of unauthorised access, even if someone manages to obtain your password.
It’s a good practice to regularly rotate your passwords as a precautionary measure. Personal information, including passwords, is often sold by malicious actors on the dark web. Moreover, centralised companies frequently experience data breaches, meaning your passwords could be out there on the internet, just waiting to be exploited. Stay vigilant and keep your online security intact!
Fast Fact:
Password managers are a great way to keep track of your passwords and avoid reusing them. They allow you to use strong and unique passwords without the need to remember them all. Some password managers even include password generators for creating strong passwords. Additionally, authenticator apps provide an extra layer of security by generating unique one-time passwords (OTP) or pins. They are time-sensitive and often send codes directly to your phone for easy login.
Connect to the Internet Securely
When using online wallets, it is crucial to employ secure internet connections like Virtual Private Networks (VPNs). VPNs can help you bypass geographical restrictions for online services, ensuring privacy and safeguarding your personal data from hackers and advertisers.
Additionally, never leave your wallet open on a public computer. Doing so could leave you vulnerable to keylogging, which is when someone uses malicious software to record keystrokes and gain access to personal information.
Keep Private Keys Offline
When it comes to safeguarding your cryptocurrencies, opting for cold storage is a much safer choice compared to hot wallets. Hot wallets, being connected to the internet, are susceptible to online attacks. While they offer convenience for using decentralised applications (DApps), cold wallets may be less convenient in such scenarios.
For top-notch crypto wallet security, hardware wallets are the way to go. These purpose-built devices are designed specifically for cold storage solutions. Resembling USB drives, they are lightweight and can be connected to a PC. Among the most popular hardware wallet brands in the market are Ledger Nano and Trezor.
Make Regular Backups
Whether you’re using a hot or cold wallet, it’s essential to ensure your peace of mind with backups of private keys and seed phrases. Protect your digital assets from potential loss by implementing a reliable backup strategy. Store that backup securely offline, away from the prying eyes of malicious hackers.
One popular approach is using recovery files, where you create an encrypted file and store it on a cloud service like Google, Dropbox, or iCloud. However, this method comes with risks as sensitive data is stored in the cloud.
Another option is multi-party computation (MPC), which involves splitting your private key between local and remote storage. While recovery kits and MPC offer convenience, they also introduce counterparty risk.
Unique methods like NFTs or QR codes can also be used to back up wallets. Additionally, social recovery is emerging as a method where trusted family or friends can assist in restoring your wallet. It’s important to note that while these methods may not be as popular or widely recognised, they provide alternative options to consider for wallet backup.
Be Aware of Scam Schemes
When handling cryptocurrencies, it’s important to remain vigilant, as fraudsters often exploit crypto users using phishing scams and other malicious activities. Be sure to double-check the website URLs or emails before clicking any links. In addition, always keep your wallet software up-to-date with the latest security patches.
Also, downloading or using services exclusively from official websites is highly recommended. Google Play, App Store, and Microsoft Store are excellent examples of platforms that thoroughly assess applications.
Final Words
It is important to remember that every user is their own biggest risk when it comes to crypto. The more you educate yourself on the intricacies and nuances of cryptocurrency, such as blockchain technology, market trends, and security measures, the smaller that risk becomes. By staying informed and continuously expanding your knowledge, you can navigate the crypto world with greater confidence and minimise potential risks.
Ensuring the security of your crypto wallet is not a one-time exercise. It requires regular maintenance and vigilance to make sure that no malicious actor gains unauthorised access to your funds. By following best practices and keeping up with the latest developments in terms of wallet security, you can ensure that your digital assets are always kept safe.
FAQ
What should I do if my crypto wallet gets compromised?
If you discover that your crypto wallet has been compromised, the initial step is to take immediate action. Start by implementing damage control measures. Change all passwords linked to your wallet account, as well as any other associated accounts. Moreover, get in touch with the wallet provider’s customer service team for additional guidance. It’s also a good idea to fortify your device against future attacks by installing security software like anti-malware programs and ad blockers.
Should I use multiple wallets to store different crypto assets?
Yes, it is suggested that crypto investors maintain multiple wallets to separate their crypto investments by type or value. By doing this, you can quickly narrow down where any suspicious activity has occurred and take the necessary steps to prevent further losses.
Is it safe to store cryptos on an exchange?
A crypto exchange is a great platform to buy, sell, and trade digital assets. However, it may not be the best place to store cryptos for an extended period of time. Exchanges are more prone to hacks and cyberattacks compared to other storage solutions like hardware wallets or paper wallets.
How can I recover access to my wallet if I lose my recovery seed?
If you lose your wallet’s recovery seed, it can be extremely difficult to recover access to your funds. The best action is to contact the wallet provider and let them know what happened. They should have a plan in place for such cases and may be able to provide further guidance on how to proceed.
Is it possible to track a crypto wallet’s activity?
Yes, it is possible to view a crypto wallet’s activity. You can use blockchain explorer tools and services to track transactions associated with a particular wallet address. Additionally, some wallets come embedded with tracking features that let you trace the movement of funds from any given address.




