What’s at Stake? Here’s How to Avoid Scam Tokens
Mar 07, 2023

Thanks to the development of crypto technology, there are all kinds of projects designed to transform the financial system and give society new ways to invest, pay for goods and services, interact with virtual reality and much more. However, such a strong hype around this technology and, as a consequence, its incredible popularity contributed to the emergence of fraud in various forms, which undermines the trust of traders and investors. One of the well-known types of fraud in crypto space is scam tokens.
This article will help you understand what a scam token is, how to define it, and the main types of scam tokens. You will also learn about a few distinguishing signs that can give scam tokens away. Finally, we will give some useful tips to help you avoid buying scam tokens.
KEY TAKEAWAYS
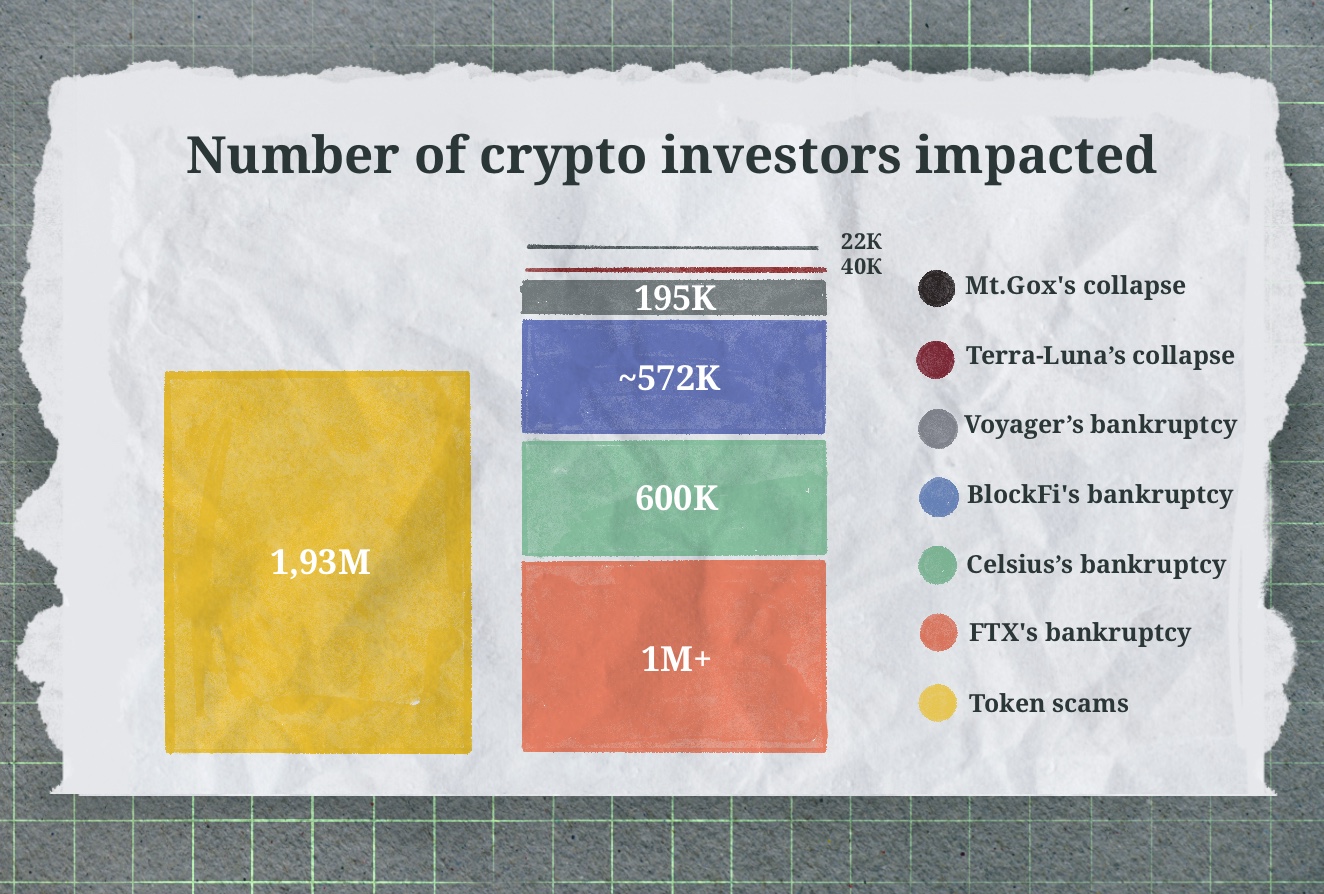
Scam tokens have hurt investors more than all the cryptocurrency exchanges collapses combined throughout their history.
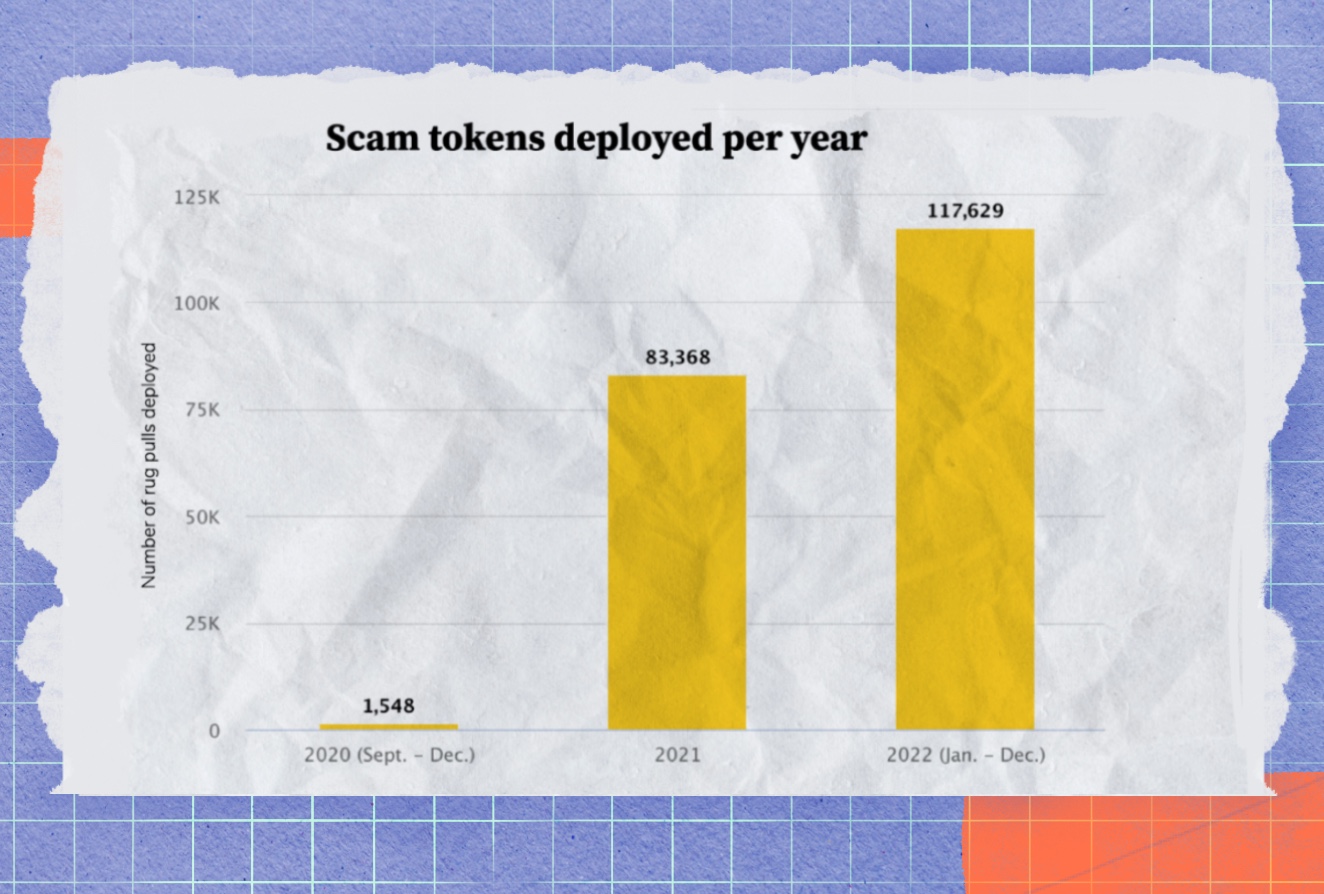
According to some reports, more than 115,000 scam tokens were created in 2022, hurting investors in one way or another and undermining confidence in the crypto niche.
There are many tactics used to verify the authenticity of new tokens. For example, it's recommended to read user reviews on various forums, check if the token is listed on crypto exchanges, as well as examine liquidity and transaction history.
What is a Scam Token?
Crypto scams are a form of Internet fraud in the crypto space that involves deceiving gullible investors. In most cases, the term is used to describe projects that have been created to siphon money. The term scam is also used to describe the actions of scammers who deceive newcomers and take possession of their assets. This is the most common scam scheme, which is unlikely to ever become obsolete.
Crypto scams thrive because of poor regulation. The specifics of blockchain are such that every transaction can be traced from sender to recipient, but it is difficult to figure out the cryptocurrency owner. Cryptocurrency scammers often operate under the same scheme — create a scam project, artificially create a rise in the price of a crypto-product, and at the peak of the price withdraw money, leaving token holders with no money.

On the other hand, very often phishing attempts are used to gain access to different kinds of data of a crypto project (legitimate token), such as login credentials, in order to send out different promotions on behalf of a well-known project, which are often called giveaway scams, and to attract the attention of investors with the subsequent deception. In this case, the scammers come up with different schemes to lure investors' money, and then disappear, leaving no trace behind.
According to The 2022 Rug Pull Report, more than 117,000 scam tokens were created in 2022, hurting investors in one way or another and undermining confidence in the crypto niche.
According to the same report, scam tokens have caused more damage to crypto investors than the most high-profile and well-known crypto exchange bankruptcies combined.
How to Identify a Scam Token
As scammers create more and more clever schemes to cheat, it becomes more and more difficult to detect fraudulent worthless tokens in DeFi. To avoid scam tokens, you need to do your own research and thoroughly analyze each new token you are going to invest in.
Today, there are many online resources that help to conduct a comprehensive assessment of the authenticity of any crypto project or token.
Dextools
Dextools works with Ethereum and Binance Smart Chain and is a great platform to quickly assess token activity. Once you find a token's contract address, you can sort a list of all token purchases and sales by selecting the "Type" category. If the token has no sell orders, chances are that you have run into a honeypot, or there is some kind of restriction on selling.
Etherscan
Etherscan is a notebook for the Ethereum network. Etherscan is an exceptional service that shows all actions in the Ethereum network, such as public data about transactions, smart contracts, addresses, and other information. Etherscan lets you see how much and what cryptocurrency any address has sent and received. You will also be able to find and check any smart contract (if its code is open to all) and see the balance of any address.
BSCScan
BscScan is an analytics service for the Binance Smart Chain network. It can be used to find transactions and check their status; monitor new blocks in the chain; check balances and view transaction history; search, read, and use smart contracts provided by the blockchain; and study bargain token offers.
The service provides public information about blockchain activity. You don't have to have advanced knowledge to find the crypto coins you want. Registration is not needed to view basic public data, but you must register for free to access the site's content fully.
In addition, there are other tactics you can use to verify the authenticity of new tokens. For example, you can read user reviews on various forums, see if the token is listed in browsers and on crypto exchanges, as well as examine liquidity and transactions using services such as CoinMarketCap or CoinGecko.
Common Types of Scam Tokens
Frauds in the crypto sector, especially related to crypto tokens, have become very popular with the development of blockchain technology and the emergence of decentralized finance. Speaking of scam tokens, there are several basic types that make up the common scams group.
1) The Exit Scam
An exit scam is a trick in which projects disappear (or close) after investors deposit their money. An exit scam is an event in which a cryptocurrency project disappears along with investors' money during or after the ICO period. In other words, whales try to pump up the price in parallel with advertising and promotional activities, only to dump their coins later. Such events are quite difficult to detect until they happen, similar to a black swan event, but they happen more often than the latter.
2) Airdrop Scam
An airdrop scam is a method used by scammers within specific tokens to reach many users, as millions of investors wait to participate in an airdrop to get free cryptocurrency. This means that a project can gain notoriety in a short time simply by giving away a scam token. This process is usually part of each new cryptocurrency's initial coin offering (ICO) or founding moments. Such a method of fraud is one of the most popular.
3) Pump and Dump
A scheme to artificially increase a cryptocurrency's rate (Pump), followed by a price collapse (Dump). In this scheme, scammers sell new unknown tokens, convincing investors that the prices will rise soon. To raise the cryptocurrency rate, the scheme organizers actively use advertising — specially created websites. After a rush occurs, the fraudsters wait for the asset's price to rise due to high demand and then sell their tokens sharply. As a result, the exchange rate collapses, and other cryptocurrency holders are left with depreciated assets.
FAST FACT
OneCoin is considered to be the best-known coin scam in history, which collectively caused more than $4 billion worth of damage to investors.
Other Red Flags That Point to Scam Tokens
If you do not know about the ways to avoid crypto scams, such scams can become an unforeseen problem for all your investments. However, besides using basic methods to expose scam tokens, you need to know about some warning signs that will help you to understand that you are dealing with a fraud.
The Promise of Astronomical Profits
As a rule, scam projects (including tokens) promise their investors fabulous returns in the form of hundreds or even thousands of percent of the initial investment after the launch (ICO). Many newcomers to crypto investing are very gullible and are chasing easy profits. This is an ideal scenario for fraudsters and attackers who intend to steal funds from unsuspecting victims. It is necessary to always remember that there is no easy and quick earnings, and any communication of golden mountains in investing is always a fraudulent scheme.
Requests to Invite More Friends
Asking friends and family members to use a product or service is a common marketing strategy for attracting new customers in any business. Often this method of business development is perceived quite calmly, because in this way the company seeks to expand its active audience. The same tool, however, is used by scam projects to attract as many investors as possible, so they can get the most benefit possible. To prevent this, it is necessary to carefully check the project before thinking about investing in it.
Requests to Report Secret Information
Regardless of the project in which you invest, the project development team will never, under any circumstances, require you to tell your financial information in the form of private keys, secret phrases and passwords. Scam projects that are interested in stealing investors' money sometimes extort confidential data in order to gain additional access to crypto wallet credentials and other secure places to store digital assets. It should be remembered that no private data related to the security of crypto assets and other personal account data should be disclosed.
Tips for Avoiding Scam Tokens
Cryptocurrency fraud has quickly become a big problem in investment activities aimed at generating profits from various crypto projects. For example, staking crypto is one of the most popular forms of capital appreciation, as well as a prime target for crypto criminals looking to profit from gullible inverters. In order not to get caught in the trap of criminals and avoid crypto scam, here are some useful tips.
1) Keep a close eye on website URLs
Every crypto project has its own website which contains all the necessary information about it. As a rule, scammers and cyber criminals use different kinds of software and applications that allow them to create an exact copy of the project website, but with a change in the name of the site. Often unsuspecting investors do not pay attention to the name of the site, because the changes are not visible when opening the site. This can be seen after it became clear that the project has the nature of scam and is trying to swindle investors.
2) Take advantage of multi-factor authentication
Security has always played an important role in ensuring the safety of funds, not only in the crypto world, but in the entire financial sector. Since many fraudsters are always looking for security vulnerabilities in certain objects of financial infrastructure (wallets, access keys, secret phrases, etc.), it is necessary to pay due attention to ensuring a high level of crypto assets security. By using different crypto wallets like MetaMask, you can protect yourself from possible unauthorized capture of your data.
3) Do your study
Comprehensive analysis of each individual token's activity can help prevent the theft of funds from your crypto wallet. Since information about each crypto project is in the public domain, you can always find all the comprehensive data about the project (token), including its statistical and analytical data, creation and development history. You can also view tokenomics, reviews and social networks that the project has. Such research will help to understand what potential the token has and whether it contains any suspicious activity.
4) Be careful who you trust
Today, very often, you can see how the purchase of a particular token is purely advisory in nature. It happens that many investors decide to buy only on the basis of recommendations and advice from third parties whom they do not know, but trust their assets. Such behavior in many cases leads to loss of funds because people who give such recommendations are often fraudsters who are interested in attracting as many investors as possible to their project. To avoid such a problem, you need to be able to check any information coming from third parties, as well as check sources that contain any information about the project to make sure the project really exists and does not pose a threat.
5) Make sure your crypto wallet is secure
Crypto wallet is the main tool for working with cryptocurrency assets. The choice of wallet plays an important role because it is the main storage of all crypto investments. Also, an important point is its security, which you need to pay special attention to. It is much worse to lose assets as a result of hacking than to forget a password or a secret phrase, which can be restored later. Be sure that the wallet you choose offers all the necessary tools to protect both personal data and your assets.
Conclusion
As crypto technology has become a real gold rush that has allowed to extract huge profits from the crypto market, it has become a clear signal to many fraudsters and cyber criminals to steal crypto assets from investors. Therefore, it is crucial to take all necessary measures using all available tools in order to avoid scam tokens, protect yourself from theft and preserve your digital assets while interacting with the crypto sphere.




